Security Remember Ransomware? Don’t fall victim even if…
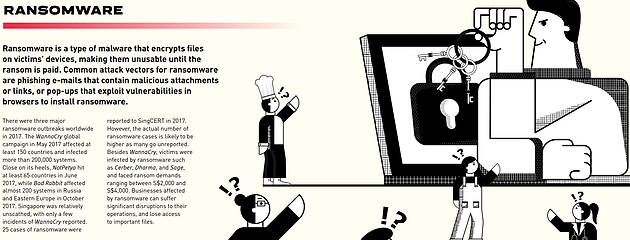
Picture from CSA of Singapore
2017 was a field year for many on both side of the line.
Virus writers, cyber criminals and syndicates introduced ransomware to the world and it was reported that many crooks made a lot of money. On the other side of the line were the victims who paid the ransom to get their stolen goods back.
Many endusers might have forgotten about it though this happened barely a year ago. You could visit a blogpost we wrote back then..
To our knowledge, several cases surfaced recently from ransomware viruses. The challenging part of falling victims is that, many of these malware are not new. Even their names remain the same. And endusers still fall prey.
There are probably many scenarios which ransomware can claim victims. What we hope is to provide additional basic information and methodology for enduser and hope that can minimise their exposure and possible damage.
Below are some quick pointers in addition to those in the previous blogpost…
- For Microsoft or Windows-based systems, please update patches and hot fixes. This cannot be stressed enough. Those on open source system does not mean patches can be done without. Please also check for updates
- Invest in sturdy antivirus protection. This doesn’t have to cost an arm or a leg. How to know what you intend to invest in is sturdy enough? Don’t purely depend on online reviews. Discuss with your IT peers. Or give us a call
- Be mindful of file extensions like .exe, or .scr. Enable file extension on your computer can help to spot any suspicious file names
- Disable smb v1 in your network. This is a showstopper for WannaCry
- To add on to point one above, not just Microsoft software, update all software in your eco-systems
- Go unplugged. This is not related to songs and singing. If you discover any unusual activities in your systems, unplug yourself from the network quickly to reduce virus expansion
- There you go. Hope these help to bring up your antenna when confronted with ransomware.




