Security – Beef Up Your Defences Without Burning Holes..
Iron-cladding IT security can be expensive.
Depending on the type of security mechanisms, what are the digital properties to protect and to some extend, what is the tolerance from key stakeholders.
Whichever security option is chosen, it is important for users and entities to protect themselves by adopting appropriate technologies and work with the right partners.
As one of our GTM partners, HPE has been intensifying its moat into this area.
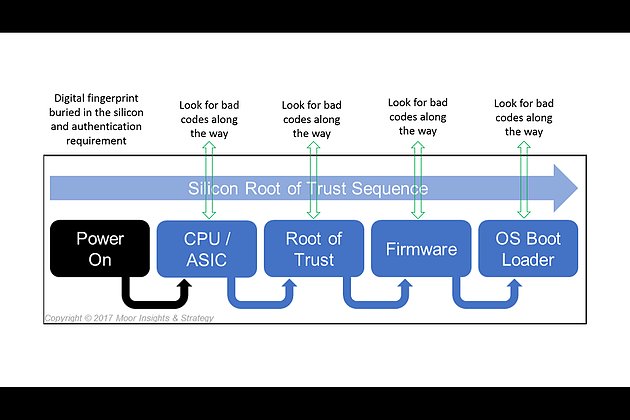
At the basic level, known broadly as Secure Compute Lifecycle, the technologies embedded into HPE Gen10 servers map into National Institute of Standards and Technology’s (NIST) stringent framework.

HPE’s silicon root-of-trust component achieves the highest level of secure technology by NIST in what is known as Commercial National Security Algorithms, or CNSA.
In a boot-up sequence, when a user powers up a Gen10 server, instructions are sent through to each stage with an authentication procedure. Each pass-through requires checking for anomalies and unusual entities.
If a hacker embedded a virus into the chain of command, the silicon root-of-trust then kicks in to alert the IT administrator about the breach.
As a partner, EDS works with HPE in lock-steps right from the start in a consultative approach to client’s existing infrastructure, maps into client’s businesses and operating models, draws up plausible network and system architectures which fit into current settings and how they may scale into future requirements.
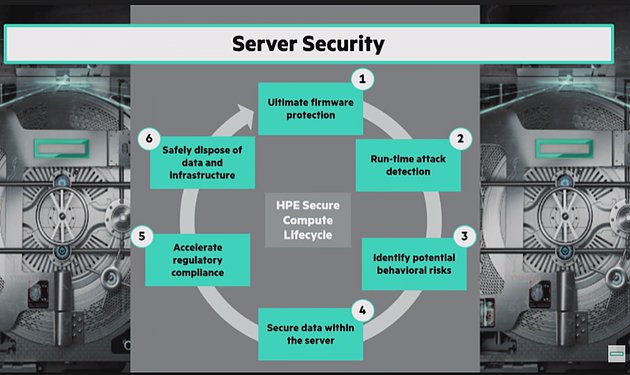
This methodical approach is aimed to serve and drive towards a mutually-beneficial outcome for stakeholders. But it is only one perspective of a broader spectrum.
Many organisations have been “lost” when it comes to approaching cyber security in a pragmatic way. Who can blame endusers if they are confounded!? From certain angles, cyber threats can be different from just 12 months ago.
Many organisations are faced with frustrating choices in tackling cyber menace vis-a-vis finance outlay and protecting investments.
The methodologies we adopt come from multiple lenses, map into client’s current situation and where pragmatically possible, keep in focus of the future where clients might go.
Take a quiz by following this link to learn more..





